One control plane for every AI model
Multi-tenant MCP gateway with identity-verified governance. Tenant isolation, custom connectors, built-in integrations, and a full dashboard — all powered by GatewayStack's open-source modules.
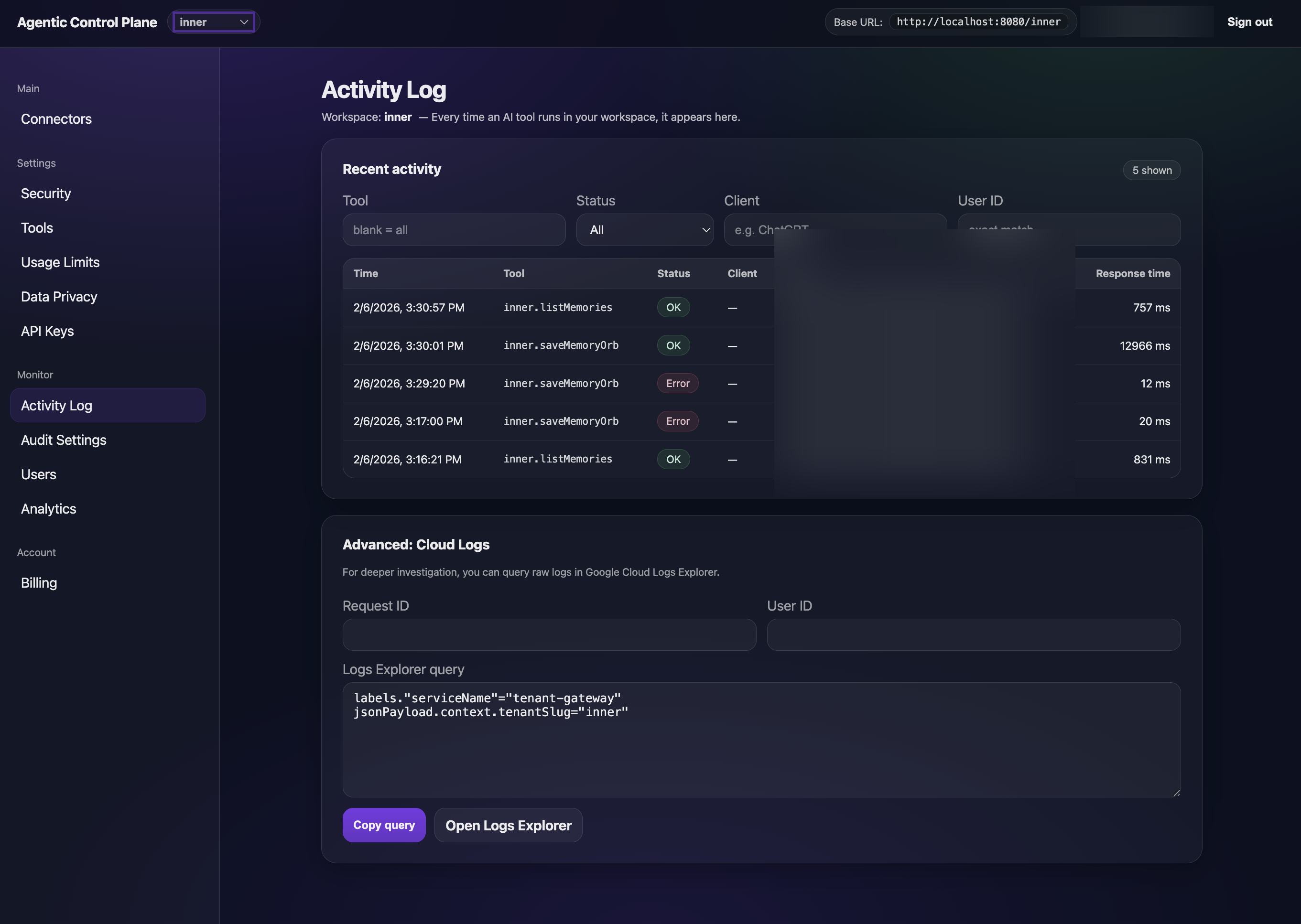
Every tool call logged with verified identity, client attribution, and latency.
Built-in connectors. Custom APIs. One URL.
Start with pre-built connectors for popular services, or point ACP at any HTTP API and it becomes an MCP tool — with auth, validation, and audit built in.
Custom connectors are defined in the dashboard — point to any URL, define the input schema, and ACP handles authentication forwarding, SSRF protection, and request validation.
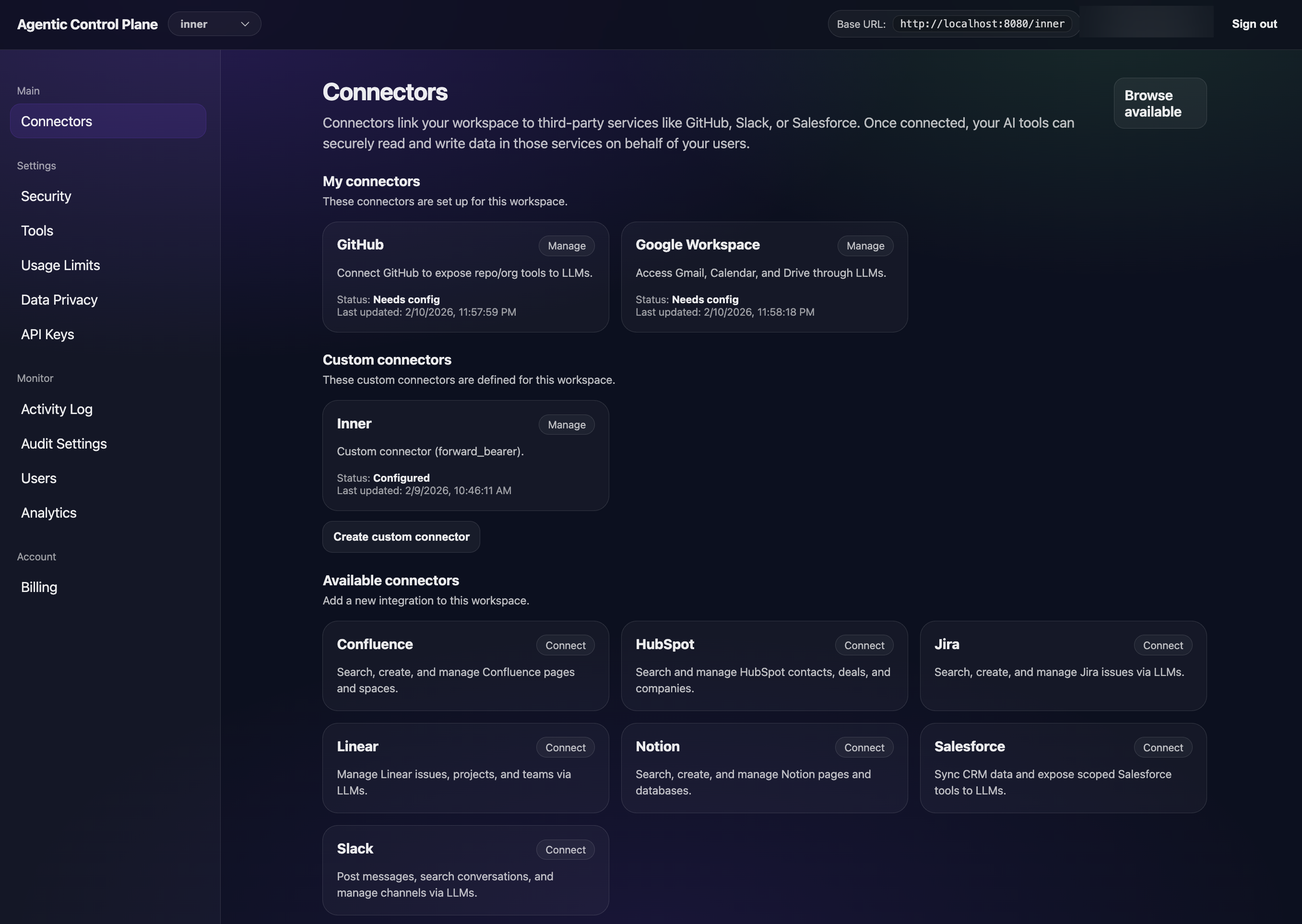
Add built-in integrations or define custom HTTP connectors — all governed by the same pipeline.
Everything you need to govern AI access
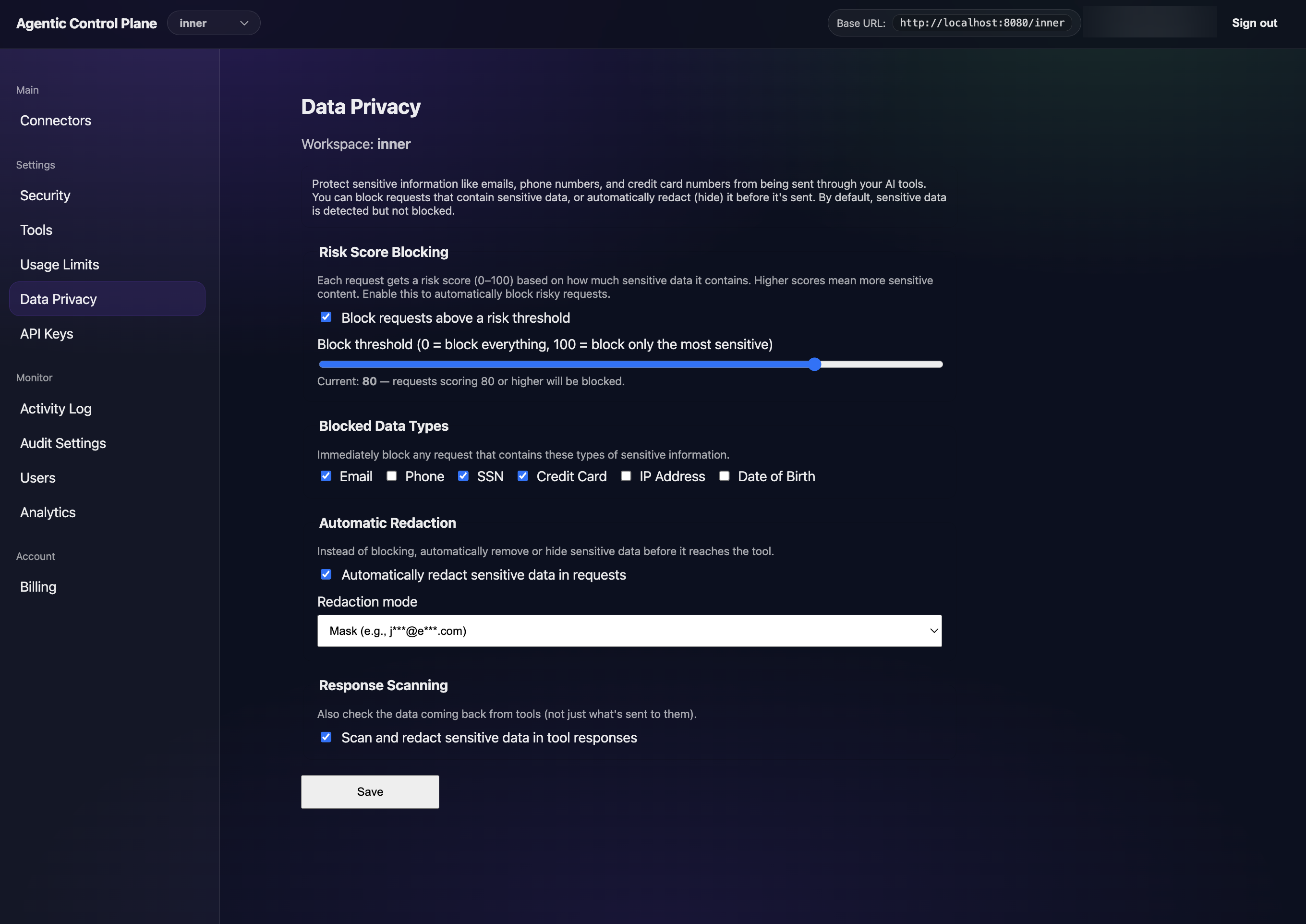
PII detection, risk-score blocking, and automatic redaction — configured per tenant, no code required.
How it works
Integration examples
Connect integrations are HTTP tools that run through the full governance pipeline. Define them in the dashboard or use built-in connectors.
GitHub — list repositories
Built-in integration. Connects to GitHub's API with OAuth token forwarding. The gateway verifies the caller's identity, checks their permissions, and logs the request before forwarding to GitHub.
auth: forward_bearer
endpoint: GET api.github.com/user/repos
scopes: tool:github:read
Custom connector — internal API
Define any HTTP tool in the dashboard. Connect injects authentication, enforces SSRF protection, and applies your tenant's policies. No code required.
auth: service_oauth
endpoint: POST crm.internal/api/customers
scopes: tool:crm:read
Built on open source
Connect runs all six GatewayStack modules in its request pipeline. Every tool call is identified, transformed, validated, rate-limited, routed, and audited — same governance engine, managed for you.
What Connect adds on top: multi-tenant isolation, a web dashboard for configuration and audit review, built-in integrations (GitHub, Salesforce), custom HTTP connectors, and deployment on Cloud Run with Firestore-backed config.
Ready to get started?
Request beta access and start governing AI access in minutes.